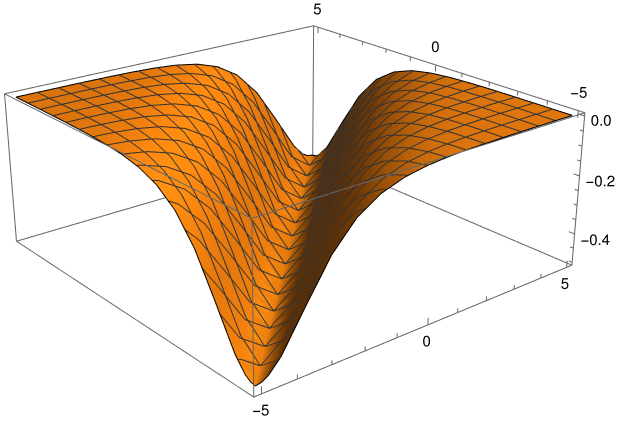
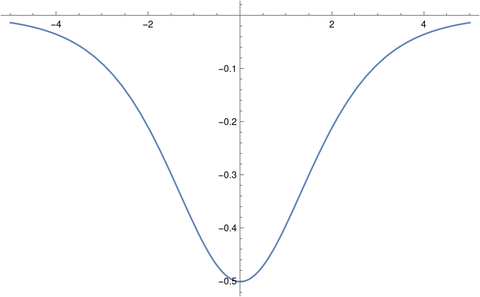
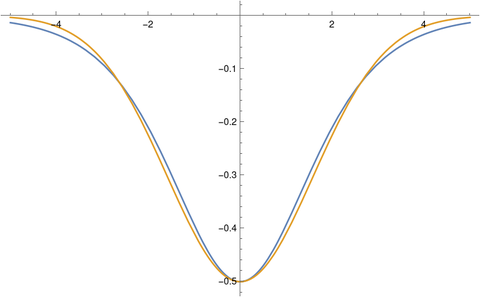
Tens of millions of fax machines still exist. My business line gets calls from modems and fax machines fairly often. Maybe my number is close to that of a fax machine.
Fax machines and health care
Fax machines are especially common in health care. I remember when I was working at MD Anderson Cancer Center someone said IT in health care is a decade or two behind business. Still, that was a decade ago.
Fax numbers are one of the 18 things disallowed under HIPAA Safe Harbor, which is one way Safe Harbor shows its age. Few people have fax numbers anymore, but if someone does have a fax number, that could be an identifier. In fact, even knowing that someone has a fax number, without knowing what that number is, could be a privacy risk because it could help narrow down someone’s identity.
Pros and cons
There are advantages to using fax machines. You can send faxes over the internet via various services, but if you send a fax over POTS then your transmission does not go over the internet. This means the transmission is not vulnerable to some kinds of attacks, but I would think good encryption would be even better [1].
Audit trails and privacy
Fax machines either provide a better audit trail or a worse audit trail. The argument for a better audit trail is that faxes are time-stamped pieces of paper, and so are better evidence than emails. That’s one reason the legal profession likes faxes. On the other hand, once you shred a fax, it’s gone. When you delete an email, it’s hard to say how many copies of that email still exist. So faxes could be good for privacy. Maybe faxes provide a better audit trail if you want to provide an audit trail, and they make it easier to avoid an audit trail if that’s what you want.
Old technology never dies
As Kevin Kelly has pointed out, technologies never die. Of course some bizarre technologies die, but a surprising number of technologies live on, long after they’re considered obsolete. When technophiles announce that a technology is “dead”, that usually means that the technology is losing market share. A “dead” programming language, for example, may have a large and growing user base, but the user base is not growing as quickly as that of other programming languages.
Technologies are multi-faceted, and it’s rare that a new technology is better than its predecessor on every facet. The use cases for which the old technology is better occur less often over time, but if they don’t go away, the old technology won’t go away either.
Related posts
[1] Encrypted email is a mess. Encrypted email between, say, two Proton Mail accounts is secure, but email between different providers is not. An encrypted attachment is less convenient and more secure.